-
Posts
1,135 -
Joined
-
Last visited
-
Days Won
51
Content Type
Profiles
Forums
Events
Downloads
Everything posted by tomnic
-
The problem with the latest Krisp versions is that no proper entitlements are copied after forcefully recodesigning the app. This is the way to run it anyway, refer to https://github.com/NyaomiDEV/AMDFriend for installing it: Code: sudo amdfriend --in-place --directories /Applications/krisp.app ...so the app will be patched but codesign not replaced (if you replace it with the --sign option in AMDFriend the app won't make you logging in because of messed up special entitlements to access the keychain during the inplace patch). Then copy to the desktop /Applications/krisp.app (which isn't recodesigned yet) and issue this command: Code: codesign --force --sign - ~/Desktop/krisp.app delete /Applications/krisp.app copy back ~/Desktop/krisp.app into Application folder, thus making sure to write it to a new inode. Double click the app, it should run and let you authenticate, tried with the new 1.40.11 version. According to this article, https://developer.apple.com/documentation/security/updating_mac_software, with some apps inplace recodesignign doesn't properly work, you need to do it to a copy of the same app, and place the app back to the original path... the bug is this: https://developer.apple.com/forums/thread/130313 @Nyaomi, just to inform you.
-
Sono limitati lato firmware nel boost delle frequenze... Forse per avere più margini di miglioramento con M2 ultra M3 etc, specie in single core dove è sempre più difficile crescere in modo massiccio.
-
Quasi quasi mi faccio ridare la Z390 😉 LoL. Dai che si scherza!!!
-
Idem con patat(a)e
-
-
Con il service pack 2 era diventato praticamente Windows 7 come affidabilità... rimpiazzato subito dal nuovo os tuttavia 😉 Lunga vita a (s)vista ^^
-
Dopo aver formattato il disco in APFS... success 😉 Alder Lake traghettato nel nuovo macOS! Potevi suggerire: stretta è la foglia, larga è la via... 😛
-
E' l'ipaddosità ormai completata di macOS, il menù preferenze mi sa caotico... sarà solo questione di abitudine vedrai
-
Sì sarà destinato a diventare lo (s)Vista di Apple
-
Qualità prezzo è LA cpu Alder lake da avere
-
Millemilaaaaa
-
Ricordatevi di NON usare la Fix pat patch di Shaneee con schede nVidia... si blocca tutto! Bisogna usare per forza la più lenta tradizionale fix pat di Algrey
-
It starts perfectly on my Ryzen 9 5950x: No patches needed yet, since AMDFriend cannot find any intel specific code. Search in console app the crash log of Lightroom and post it please.
-
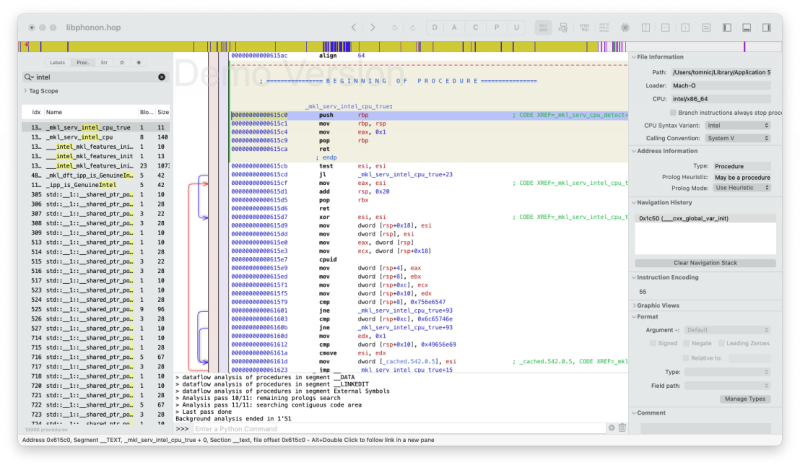
It also makes working Counterstrike GO on AMD Hackintoshes: sudo amdfriend --in-place --sign --directories /Users/tomnic/Library/Application\ Support/Steam/steamapps The lib with intel cpu check code is libphonon.dylib Routines found for /Users/tomnic/Library/Application Support/Steam/steamapps/common/Counter-Strike Global Offensive/bin/osx64/libphonon.dylib: - <53 48 83 EC 20 8B 35 99 0A F7 01> at offset 29189568 (Hex: 1bd65c0) File /Users/tomnic/Library/Application Support/Steam/steamapps/common/Counter-Strike Global Offensive/bin/osx64/libphonon.dylib was patched. Patched file location: /Users/tomnic/Library/Application Support/Steam/steamapps/common/Counter-Strike Global Offensive/bin/osx64/libphonon.dylib Finished processing file: /Users/tomnic/Library/Application Support/Steam/steamapps/common/Counter-Strike Global Offensive/bin/osx64/libphonon.dylib
-
I've done the functionality test directly in Logic / Mainstage to re-enable the failed plugins after the patch
-
Perfect for the latest Waves 13.5 release, just scan the /Library/Application\ Support/Waves folder.
-
For the latest Waves 13 release this is the working method: install https://github.com/NyaomiDEV/AMDFriend Then execute this code in terminal: sudo amdfriend --in-place --sign --directories /Library/Application\ Support/Waves Give your password, rescan the failing plugins and you're done! Thanks for @Nyaomi for the really powerful script, all the info here:
-
Afferrato! Nessun problema, potresti solo aver necessità di aggiungere una ethernet se con Monterey le intel integrate delle varie mainboard fanno i capricci.
-
Come preferisci, ma la differenza di performance è di gran lunga superiore alla maggiore spesa 😉 Buon hackkkk
-
Fatti una build Z690 con i5-12600k e https://www.idealo.it/confronta-prezzi/201730081/gigabyte-z690-aero-g.html se preferisci Gigabyte tanto la iGpu su macOS non funzionerebbe nemmeno con la 11 gen e quindi la dotazione di porte integrate della mobo è inutilizzabile con macOS, a meno di scendere alla decima generazione. La dodicesima gen è anni luce avanti e funziona PERFETTAMENTE con macOS.
-
Io mi creerei un ambiente di test su un disco esterno usb con OpenCore e Monterey installati lì, c'è da perderci tempo e studiarci su come suggerito da @fabiosun, ma almeno avrai sempre il tuo sistema originario perfettamente funzionante su cui far conto 😉
-
E' corretto, macOS Catalina e successivi si avviano da Preboot anche con Clover / OpenCore