Leaderboard
Popular Content
Showing content with the highest reputation on 03/19/2022 in all areas
-
Aggiornamento: con l'aiuto di @SemanticA siamo riusciti a fare una buona configurazione con quest'hardware, funziona tutto. Più tardi (o domani se non riesco) pubblico un topic/build, potrebbe tornare utile a molti una configurazione "thunderbolt senza scheda video integrata" basata su processori moderni, un hackintosh per creatori di contenuti. 😄1 point
-
Questo metodo di mappare le porte con l'ausilio di Windows è straordinario. A chi come a me la mappatura delle porte è stata sempre un pò uno zoccolo duro, con questo sistema è impossibile fallire. E infatti con un pò di pazienza installando al volo Windows, il problema è risolto. Posto la EFI funzionante. Nessun problema anche con l'ultimo aggiornamento di Monterey che ha rilevato tramite l'update. EFI.zip1 point
-
con usbtoolbox da Win e' semplice ... le vede tutte 🤞1 point
-
Se hai pure Windows installato , scarica lo zip https://www.macos86.it/applications/core/interface/file/attachment.php?id=38800 ( trovi una breve descrizione all interno ) Dopo che hai i 2 kexts , copiali in Clover/kext/other ... rimuovi usbinjectall e eventuali patch e portlimit1 point
-
Salve a tutti, sono Fabio, utente Mac dal 2003. Sono un felice possessore di un Mac Classic del 1990, un MacPro PowerPC dei primi 2000, un MacbookPro del 2007 e un MacMini del 2010. Negli ultimi anni sono stato costretto per esigenze professionali a tornare su Windows, ma non riesco a rinunciare al mio sistema preferito. Il pc da cui vi scrivo è un Fujitsu Lifebook A557 e lo sto ottimizzando per avere un sistema perfettamente funzionante. Il mio primo tentativo andato a buon fine risale ad Aprile 2021 su Opencore e Catalina, tuttora funzionante e sempre aggiornato all'ultima versione di OSX10. La mia ultima installazione sullo stesso sistema (ma ancora su disco esterno 😛 ) coinvolge OC 0.7.9 e Monterey 12.3. Mancano solo alcuni dettagli per essere del tutto felice del risultato. Ovviamente sono qui non solo per avere informazioni, ma anche se posso condividere la mia esperienza. Grazie in anticipo a tutti!1 point
-
La nuova EFI che non parte l ho rinominata male 🤦♂️ EFI_ c e' uno spazio ... rinominala EFI e prova Per ocat devi dare il consenso Preferenze di sistema > Sicurezza e Privacy1 point
-
A ecco non avevi inizializzato il disco , aveva installato sopra HS Devi vedere nel bios ( disabilitando con -wegnoegpu la 1080) se hai da impostare la IGPU come display principale d avvio La EFI te l avevo aggiornata completa di grafica d avvio https://www.macos86.it/topic/5412-problema-avvio-pendrive-high-sierra/?do=findComment&comment=127270 Comunque usa questa EFI .zip ( senza -wegnoegpu ) Consiglio di usare OCAT ( GUIDA ) Per fixare ProperTree https://drive.google.com/file/d/1baPoyGfeJoJB_emJR8Cl-payaOlLGfIt/view?usp=sharing1 point
-
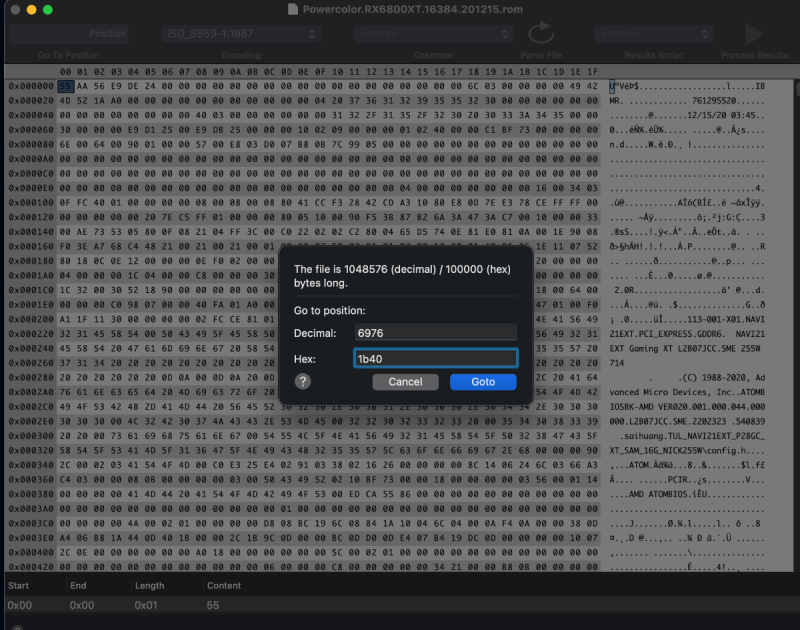
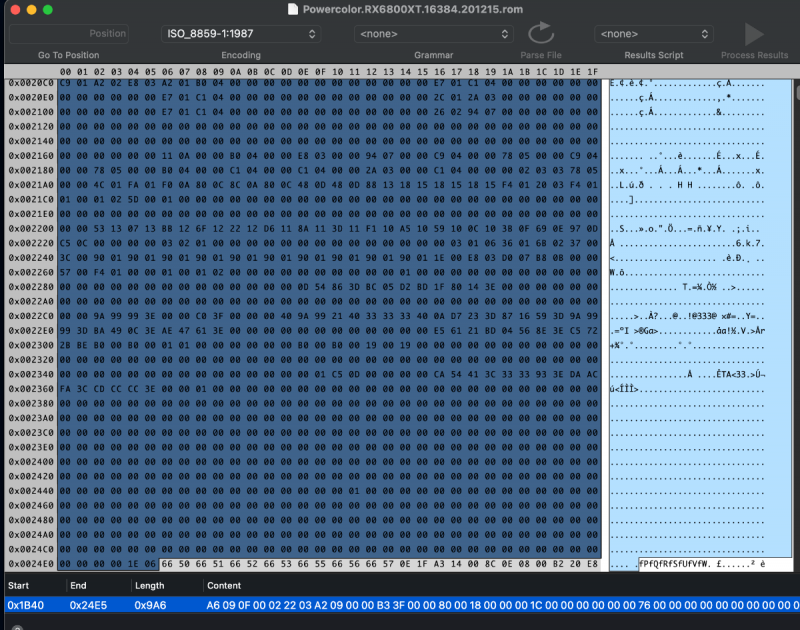
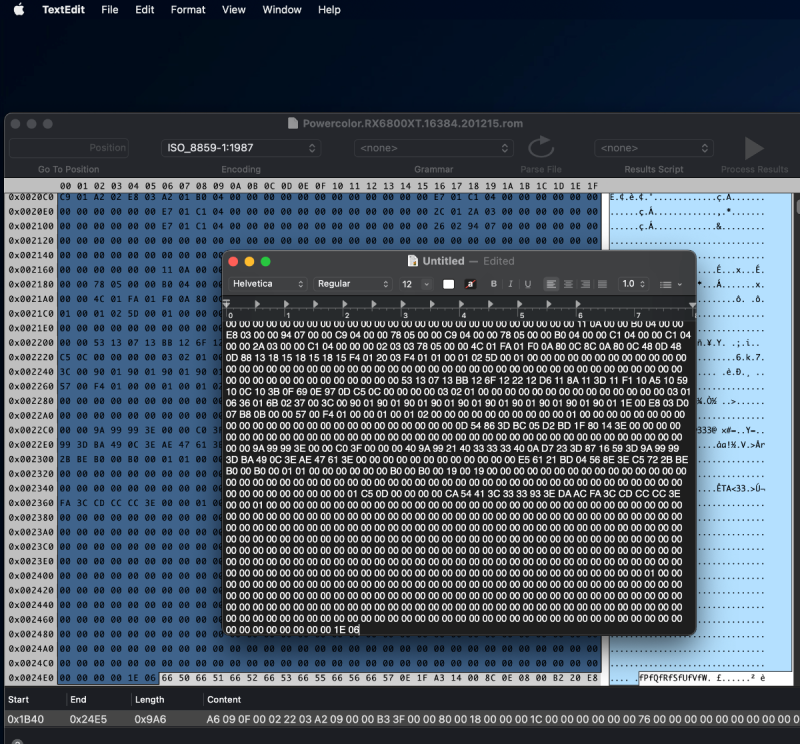
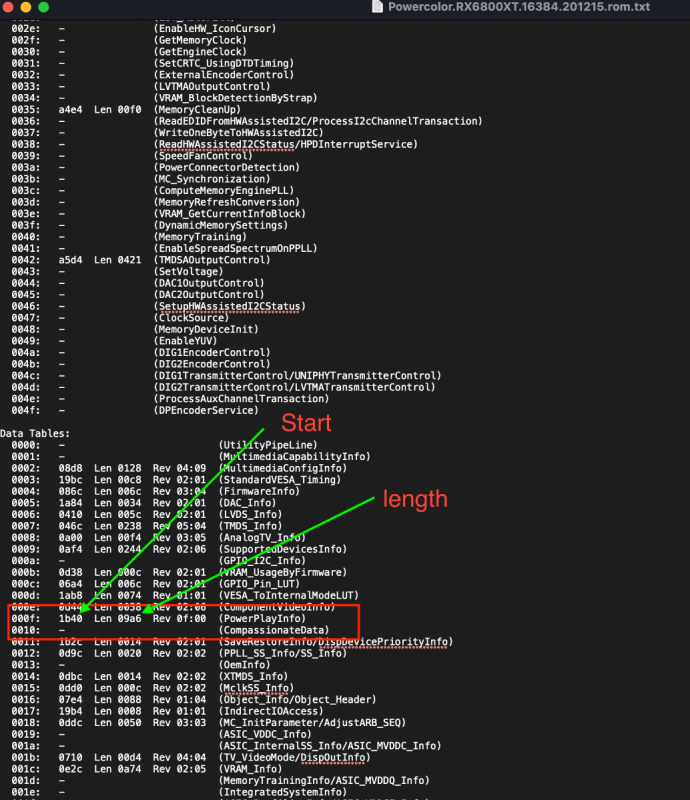
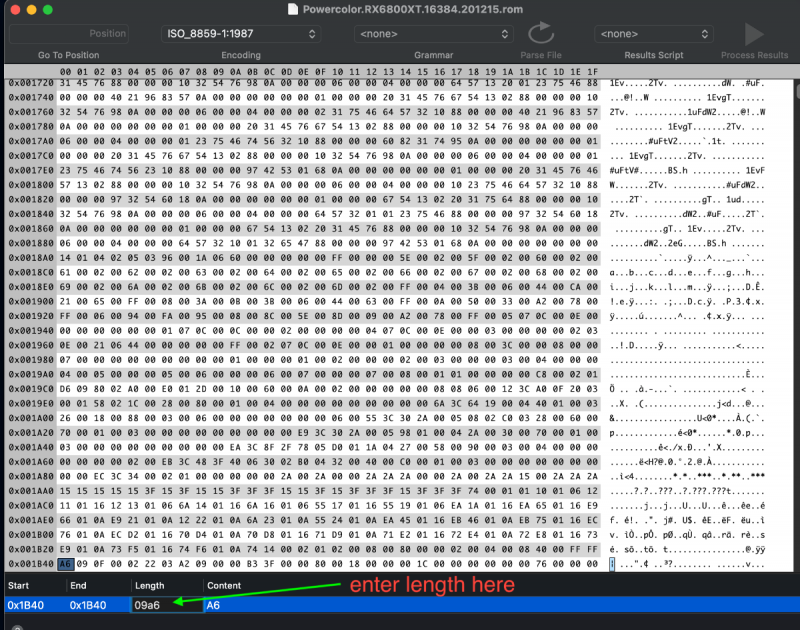
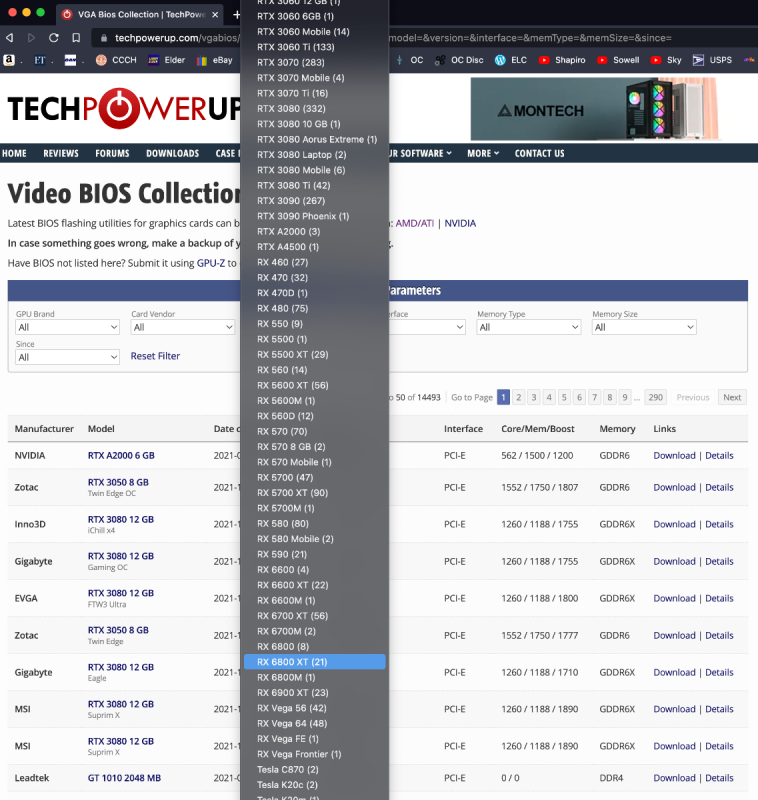
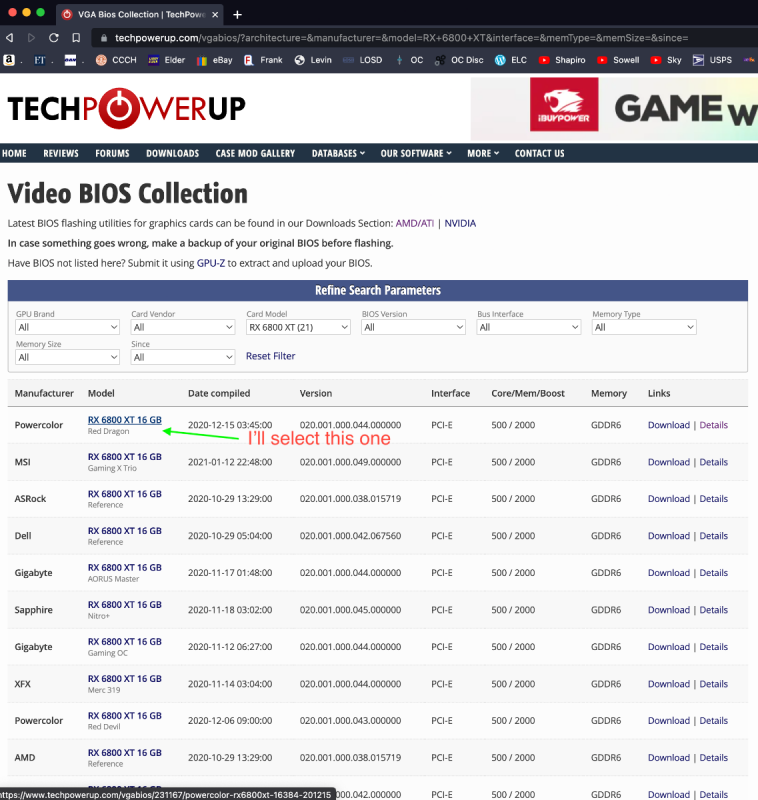
No. It is specific for each model: Radeon 6900 -> ATY,Carswell Radeon 6800 -> ATY,Belknap Radeon 6600 -> ATY,Henbury Radeon 5700 -> ATY,Adder Radeon 5500 -> ATY,Python For example, the 6900 example by fabiosun is changed from ATY,Carswell to ATY,Henbury for the 6600 model. Also, people are again playing with "PP_PhmSoftPowerPlayTable" (aka sPPT) to restore GPU metrics, also injecting via DeviceProperties. (I wrote about this early on in this thread for the Radeon VII to boost speed. The value is specific for each model.) One such thread is here. The value I use for my 6900XT (Powercolor Red Devil) sPPT: A6090F00 022203AF 09000077 40000080 00180000 001C0000 00000000 76000000 00000000 00000000 00000100 00000100 00000D00 0000640A 0000B004 0000E803 00009407 0000F204 0000C505 0000F204 0000C505 0000B004 0000C104 0000C104 00002A03 0000C104 00000000 00000000 00000000 0000F401 0000E001 00006100 00002602 00003D01 00006B01 00003D01 00006B01 0000A201 0000E701 0000E701 00002C01 0000E701 00000000 00000000 00000000 00008100 00001000 00001E00 00000101 01010101 01010101 01010101 00010000 00000000 00000000 00000000 0000B80B 0000B80B 00000000 00000000 00000000 0000B80B 00003304 00003304 00000F00 0000E40C 0000E40C 00006400 00006E00 00000100 00000100 00000100 00000100 00000100 00006400 00006400 00006400 00006400 00006400 00006400 00006400 00006400 00006400 00006400 00000000 00000100 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000F401 0000F401 00000000 00000000 00000000 0000F401 0000A202 0000A202 00000A00 0000FA00 0000E803 00001900 00003200 00000000 00000000 00000000 00000000 00000000 00001900 00000A00 00001900 00000A00 00001900 00000A00 00001900 00000A00 00001900 00000A00 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000600 00000600 06005700 5A005F00 5A00E803 B004D606 0807D007 D007CA08 CA080000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000600 0000FFFD 7FA36337 0000FF00 00000000 00000000 00000000 0000FF00 00000000 00000000 00000000 00004001 37000000 00006400 6E006400 73007300 73007300 00000000 00000000 00000100 00000A00 00000000 00000000 00000000 00000000 00000000 00000000 0000FE38 0000730F 00006400 64001C0C 800C0000 00000000 0000E40C E40C5C12 F8114000 00013200 3C00800C 800C800C 800C1400 14000000 02000000 803F0000 0000B537 B83EEF1B 67BF4F40 A73F8B04 00000000 0200EE7C 8F3FA69B 843E4434 9A3E43AD 09BE3D0F 363FF100 00000001 0400CDCC AC3FE3A5 9BBD6F81 E43ECAA6 CCBE0421 493FC001 00000000 02000000 803F0000 000072C4 7A3E4C89 84BEDCBA 433F1102 00000000 0200098A AF3F295C 0FBD85CE EB3E10CC C1BE4720 463F9B01 00000000 02006ADE 893FB81E 053E8E75 913E2849 57BEE42C 3C3F7301 00000000 0200098A AF3F295C 0FBD85CE EB3E10CC C1BE4720 463F9B01 00000000 02006ADE 893FB81E 053E8E75 913E2849 57BEE42C 3C3F7301 00000000 02007D3F 953FDD24 063E1D77 AA3EEE77 68BEC91F 3C3F5501 00000000 02006ABC 743FAE47 613E732E 653E52ED 13BED72F 383F4301 00000000 02006ABC 743FAE47 613E732E 653E52ED 13BED72F 383F4301 00000000 02000E2D 123F9A99 D93E2783 A33D8D28 EDBCE7E3 323FB600 00000000 02006ABC 743FAE47 613E732E 653E52ED 13BED72F 383F4301 0000F401 640A0000 00000000 00000000 00000000 00000000 00000000 00000000 00006B01 C5050000 00000000 00000000 00003D01 F2040000 00000000 00000000 0000E001 B0040000 00000000 00000000 00006100 C901A202 E803A201 B0040000 00000000 00000000 0000E701 C1040000 00000000 00000000 0000E701 C1040000 00000000 00000000 00002C01 2A030000 00000000 00000000 0000E701 C1040000 00000000 00000000 00002602 94070000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000640A 0000B004 0000E803 00009407 0000F204 0000C505 0000F204 0000C505 0000B004 0000C104 0000C104 00002A03 0000C104 00000002 03037805 00004C01 FA01F00A 800C8C0A 800C480D 480D8813 18151815 1815F401 2003F401 01000102 5D000100 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00002A16 D7158415 3015DD14 8A143614 E3139013 3D13E912 9612B111 CC10E70F 020F0000 00000302 01000000 00000000 00000000 00000003 01063601 6B023700 46009001 90019001 90019001 90019001 90019001 90011E00 E803D007 B80B0000 5A00F401 00000100 01020000 00000000 00000000 01000000 00000000 00000000 00000000 00000000 00000000 00000D54 863DBC05 D2BD1F80 143E0000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00009A99 993E0000 C03F3333 13400000 20406666 46400AD7 233DDD24 863DA245 B63D39B4 C83DC74B B73E7593 983D2FDD 84BEA392 7A3EE561 21BD0456 8E3EC572 2BBEC000 C0000101 00000000 0000C000 C0001900 19000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000001 3B0B4501 00003480 373B9FAB CD3EED0D 3E3C7593 F83E0000 01000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00010000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 1E06 It is injected as "Data" type; shown below for the 6900: *** Brief ROM-sPPT Extraction Tutorial The methodology used in creating the sPPT data from a ROM file are described in steps A-D below. The steps are not complicated but do seem to require working in Windows for at least one step. I've extracted sPPTs for a typical 6600 and 6800 XT GPUs presented at the bottom of this tutorial. These are native extractions and not enhanced versions, so should work with similar boards. A. Download the ROM file. From TechPowerUp, the file for the 6800XT was downloaded as shown in Spoiler below: B. Locate the sPPT section from the ROM file. I used ATOMBiosReader on Windows to process the downloaded ROM file. When you run ATOMBiosReader, you load the ROM file and immediately there will be a *.txt file created adjacent to where ever the ROM was loaded where "*" is the name of that ROM file. You can now exit ATOMBiosReader. You can continue working in Windows or transfer the *.txt file back to your Mac for the next steps. In Spoiler below is an example for the 6800XT from the txt file created by ATOMBiosReader. The whole purpose of using ATOMBiosReader is to find the start and length of the sPPT section. C. Extract the sPPT section from the ROM file. You next load the ROM file again, but now into a hex editor. This step can be done back on the Mac (such as with 0xED or Synalyze It! Pro) or in Windows using HxD. Using Synalyze, the Spoiler below shows the next step for the 6800XT: D. Sample results of the above extractions. These were derived after pasting the sPPT values into the OC config file and re-copying them prior to pasting below.1 point
-
Hi, you can use this excellent patcher built by our brilliant user @Nyaomi, follow her GitHub to install it: https://github.com/NyaomiDEV/AMDFriend To discuss about it you can write here: After having installed it close discord, then just issue this command in the terminal: sudo amdfriend --in-place --sign ~/Library/Application\ Support/discord/0.0.266/modules/discord_krisp/discord_krisp.node Put your password, restart discord and you're done!1 point
-
1 point
-
1 point
-
I present you with AMDFriend, a command-line tool that is the perfect combination of @tomnic 's guide on patching libraries for AMD hackintoshes and laziness and desire for simple automation. As stated in the GitHub page: Up to date instructions on how to install, update and use it are on GitHub: https://github.com/NyaomiDEV/AMDFriend. This in no way replaces manual patching (for now), as a human's eye and brain are certainly more capable than a pattern matcher; but it already successfully patches some common libraries (found in After Effects, Photoshop, Premiere Pro, Discord, possibly more). So, why is this different than the commonly used `perl` commands? For starters, this actually uses regular expressions as they are supposed to be used, meaning that it always matches a pattern and it never matches an exact string or set of strings. This gives it the ability to be flexible across programs and different revisions of the same program; something that wasn't achieved before. To be clear, this kinda usage is achievable with just `perl` commands, but having a tool to do it instead of long commands is always nicer. What's the immediate future of this tool? I hope to reach a point of general stability where it matches at least the super common stuff super reliably, and the less common stuff more or less reliably; I hope to achieve this with community contributions, since I don't own a lot of software to test the tool with, so if you have a need-to-be-patched application please report back! And what are the mid term plans? After the tool reaches general stability, I will probably write a simple GUI in Electron that will be used to make the tool appealing also to non-tech-savvy users, and it will also cut the need to worry about Homebrew, NodeJS and Yarn being installed in the system. Around this time, I hope to get the tool into a position to be stable and as fast as possible, so that more things can be done about patching (for example, dragging an application to the tool's window to patch all of its AMD-unsafe libraries). Credits @tomnic and @fabiosun since they were the initial testers (as a surprise to no one, I guess); also tomnic wrote the initial guide and that's like the whole point of this tool existing.1 point
-
Ho smontato l'SSD con Monterey e montato uno provvisorio su cui sto installando Windows al volo. Ci provo con un pò di pazienza. Se riesce riposto la EFI funzionante.0 points